🧠 Cognito in Multi-Region AWS Architectures — What’s the Right Approach?
When you start building systems on AWS, Cognito looks like the perfect choice for managed authentication:
- Fully hosted user management
- Secure, standards-based (OAuth2, OIDC, SAML)
- Tight integration with the AWS ecosystem
But when I began designing a multi-region architecture, I ran into one of Cognito’s biggest limitations:
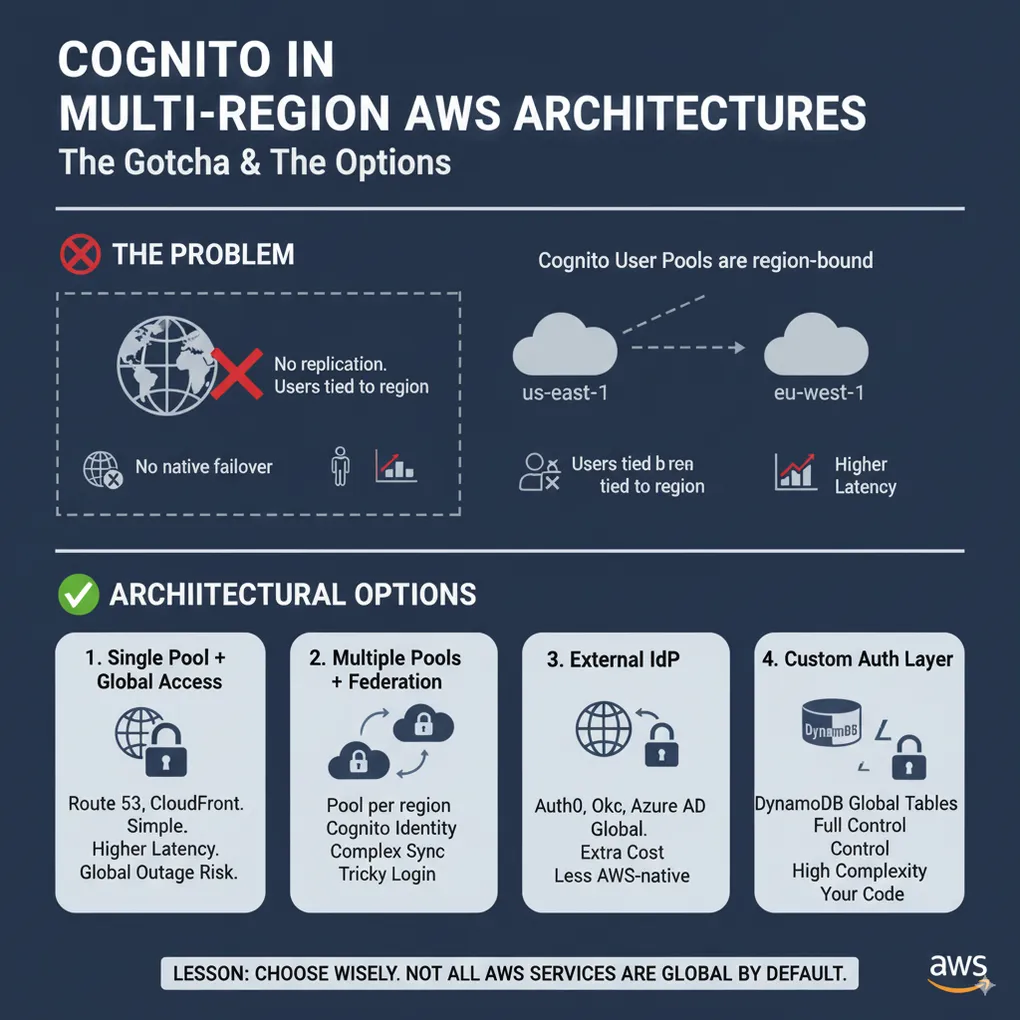
🚫 Cognito User Pools are region-bound.
- No cross-region replication
- No native failover
- Users are tied to the region where they sign up
So if a user creates an account in us-east-1, they won’t exist in eu-west-1. And that’s a deal-breaker for many global architectures.
Why This Matters
This limitation shows up in real-world scenarios:
- 🌍 Active-active deployments: serving traffic from multiple regions for low latency
- 🛡️ Resilience & DR: needing to fail over cleanly without losing user identities
- ⚖️ Compliance: storing user data in-region (e.g., GDPR, data sovereignty)
- ✈️ Roaming users: customers who travel and expect seamless logins globally
At first, I thought I was missing a hidden setting or replication option. But after deep research, I confirmed: Cognito doesn’t support it out of the box.
Common Approaches
When faced with this, you’ve got a few architectural options. Each has trade-offs:
1. Single Region with Global Access
- Pick one region (e.g.,
us-east-1) and keep all Cognito users there. - Use Route 53 latency-based routing + CloudFront to reduce access impact.
Pros:
✅ Simpler setup
✅ Full feature parity with Cognito
Cons:
❌ Higher latency for distant regions
❌ Region outage = global outage
2. Multiple Pools + Federation
- Create a user pool per region.
- Use Cognito Identity Federation or a custom IdP to link accounts.
Pros:
✅ Regional data compliance
✅ Users authenticate closer to them
Cons:
❌ Complex federation logic
❌ Syncing attributes & passwords is tricky
❌ Adds login flow complexity
3. External Identity Provider (IdP)
- Use a global IdP like Auth0, Okta, or Azure AD B2C.
- Cognito becomes optional — or is bypassed completely.
Pros:
✅ Mature, global IdPs handle replication
✅ Richer auth features
Cons:
❌ Extra cost
❌ Less AWS-native integration
4. Custom Authentication Layer
- Build your own authentication service on top of DynamoDB Global Tables (or Aurora Global Database).
- Store user identities in a replicated datastore and handle auth logic yourself.
Pros:
✅ Full control
✅ Native global replication
✅ Can align with business-specific needs
Cons:
❌ You own the complexity (tokens, password resets, MFA, security)
❌ Higher maintenance overhead
My Approach
In my case, I needed active-active multi-region deployments for resilience and latency.
I ended up building custom authentication backed by DynamoDB Global Tables:
- Global user table replicated across regions
- Lambda functions for login, signup, token issuance
- API Gateway as the front door
- Custom logic for MFA and password reset
This gave me full control and seamless user experience across regions.
But I also had to own the complexity that Cognito usually abstracts away.
Lessons Learned
- Cognito is great for single-region or simpler architectures.
- For multi-region: you must choose between complexity, cost, and control.
- Don’t assume AWS services are multi-region by default — many are region-scoped.
Final Thoughts
Cognito’s region-bound design is a gotcha for teams planning multi-region systems.
If you’re starting fresh:
- For simplicity → single pool, global access
- For compliance or low latency → multi-pool federation or external IdP
- For maximum control → custom auth service
💬 I’d love to hear your take.
Have you solved Cognito’s multi-region challenge differently? Would you stick with Cognito, federate, or ditch it altogether?